
In current IT world, data is huge. In order to handle this huge amount of data, traditional databases were incapable. This problem is solved using the large databases like Hadoop Distributed File System (HDFS). But even if you use this file system. There are some issues like security. Do you think security is an issue? Yes, security an issue in the current It world. Because, the data which transferred across the network not a homogenous data, instead, it a heterogeneous data. Today, in this article, i will you know How security is achieved using KERBEROS.
This heterogeneous data contains various forms of data like text information, image and some other confidential data like passwords.While transferring this confidential information, there is a chance of attacking the file by an unknown person over the internet. In this scenario How do the transfer the security files over the internet? The solution is the use of KERBEROS protocol.
Know more about Security in data transferring from OnlineITGuru through Hadoop Administration online Course.
Before going to know How Security achieved using KERBEROS let me introduce the basic terminology in network security.
Terminology:
Session:
It is the period of time where some particular event happens over there. This session may usually for few hours. This word is particularly used to convey that particular task will be complete over that time.
Encryption :
As we discussed earlier, transferring confidential over a network not good.So to overcome this problem, we usually, encrypt the data, to transfer over the network. Basically, Encryption is the process of the changing the data from its normal form. The advantage of this encryption is that the hacker that, this is the original of data. But it actually coded in a separate form.This coding sequence will be known only to the end user (receiver )
||{"title":"Master in Hadoop Admin Training","subTitle":"Hadoop Admin by ITGURU's","btnTitle":"View Details","url":"https://onlineitguru.com/hadoop-online-training-placement.html","boxType":"reg"}||
Decryption :
It is the opposite form of encryption. It decrypts (converting the coded data into original form) the data in order to know the exact confidential data sent by the sender
Ticket :
The number generated by the server for the purpose of identifying itself to the client (or) end user. Usually generated, to notify the receiver, that the data sent by the authorized person only. Each ticket is generated for each session.
Now let me take you to the main concept.
How security is achieved using KERBEROS:
Hope my dear readers, you got a basic idea regarding the basic terminology in networking. Now I’ll let you know the complete picture of How data transferred over the network using Kerberos and How security achieved using KERBEROS.
Basically, this KERBEROS consists of two main components
- Authentication server
- Ticket granting ticket
Initially, when a client (or) an end user wants to access the data over the network. The person not authorized to access the data immediately.
- For this, he usually sends a request to getting Ticket granting ticket from KDC.
- Now KDC will generate a TGT (Ticket Granting Ticket ) and a session key.
- Bundle this TGT + session key and send it t the client.
- At the client side, this decrypts the combination.
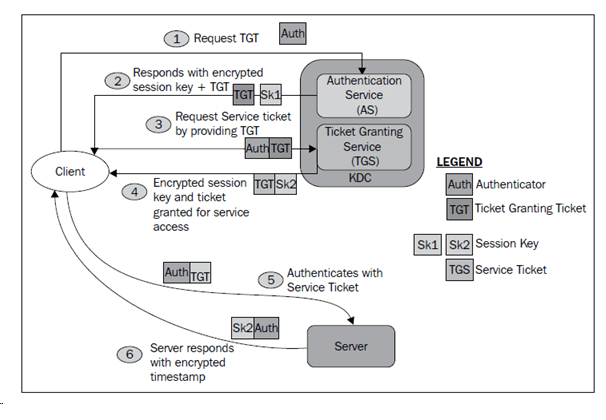
- the client needs to request the service ticket for accessing the file server.
- KDC generate a SERVICE TICKET which owned by the file server.and another session key known as k2.Now, this bundle contains the service ticket and session Key 2.
- At the client side, this bundle is decrypted using the session key S1
- At this moment, the client has a ticket to access the file server. Here the client prepares a bundle. This bundle contains a (Server ticket + authenticator + session key s2). Send this bundle to the file server.
- At the server side, this bundle will opened. Here, it will authenticate the user and send it to the client.
Finally, client and servers authenticated and whatever the authentication happens between them will always be encrypted using session key S2.
Get the more detailed working of Kerberos from OnlineITGuru through Hadoop Administration online training.
Recommended Audience:
Software developers
Team Leaders
Project Managers
Database Administrators
Prerequisites:
In order to start learning Hadoop Administration, no prior requirement was needed.Its good to have knowledge of any technology required to learn Big Data Hadoop and also need to have some basic knowledge of java concept.It’s good to have a knowledge of Oops concepts and Linux Commands.