
What is Cyber security Framework?
The cyber security framework is very Flexible, prioritized and cost-effective framework. It initiated with coordinated efforts. Among the government and business. The Intentional framework comprises the practices, rules, measures. To display the safety of Imperative foundation. The committed, adaptable, and cost-effective guidance of framework. Guides, administrators of critical foundation to show cyber security. In Today’s blog cyber security frameworks, you will notice updated things about it.
Types of Cyber security Frameworks
COBIT
Generally Cobit Controls objectives for technologies and Information. A defense framework that started by ISACA. More than 7.3 % of respondents follow Cobit. ISACA is a non-profit company. Handles a certain set of practice, standards for information systems. The Group shows Cobit 5 structure is, just like. Overarching business and management Schema. For governing and handling of total Enterprise IT. Cobit 5, is the latest version of shells that released in 2012 April. Know more about cobit with Cyber security online training
ISO
It stands for International organization for standardization, which is a private limited company. A non-governmental company that publishes standards for facilitating, the world trade. Every membership comprised of representatives from standardization agencies. More than 160 countries. Along with the International Electronically Commission (IEC). ISO handles a sequence of standards for designing and handling. An Information care management computing system. known as ISO 2700 or simply known as “ISO”.
Among the users, 20 % use this framework.
Especially We have many dozens of referred standards like ( ISO/IEC 27001,27002,27003, and many more). Not to mention the sequence under 27000. known as the “codes of practice” or explanations used to support the requirements in 27001.
ISO/IEC 27001 information aegis management systems needs. The updated version published in 2012.
CIS
It stands for Critical defense Controls, less than one-half 24.7% of respondents, told they follow the critical care controls and options.
Center for Internet Security (CIS) is a non-profit company. That handles 20 critical security controls (CSC that formerly termed as SANS 20). Uniquely CSC is a complete list of cyber security risk management. Practices that intended for stopping common attacks.
Equally important, the Control options were listed in order of priority. That starts with important like designing an Inventory type of assets. Handling Errors, controlling the usage of administrative Privileges. As a matter of fact, it Knows more about CIS with IT training.
Generally, When installing controls. That has immense value, they not intended to offer total cyber defense structure. Instead, the CIS 20 every time used at alongside. That other than schemas like NIST's. As a matter of fact. The 7th version of CIS 20 controls released in March 2018.
HITRUST
More than 30 % of respondents saying. That the company followed care shell. That maintained by total health information trust alliance (HITRUST).
Not to mention, HITRUST is completely a private company. That led by representatives from some of the Bigger names in healthcare. In the first place that includes. Anthem, Humana, Walgreens, and United Health Group.
The company handles, the common security structure CSF). It is a combination of guidelines for the information aegis. That designed specifically for complete health care option.
HITRUST CSF v9.1 latest version in the schema. That published in Feb 2018.
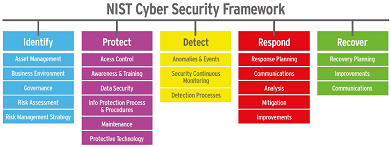
NIST
It is the popular Defense shell. In the healthcare Industry, listed as “NIST”. Which have 57.9% of total respondents report? To use their companies, deal with the NIST risk management framework.
It is the total national institute of Standards and technology. Correspondingly US agency that initiates. So many technical standards, terms, and conditions. Comparatively Which included in Information care. It is one of the US-based Department of commerce section.
NIST cyber security framework handles many documents. So, that it used widely, considered as gold standards. For total network and complete Data aegis. Typically intended to US federal agencies. They widely utilized in the private sector.
We have 3 sets:
NIST SP 800-171 that protects controlled and unclassified information. In Non-federal companies and systems. Which is revised in Feb 2018. In the first place, the Document utilized by federal agencies in another type of agreements and contracts. In general, it sets Information defense standards, followed by companies that do business with the federal government.
NIST SP 800-53: It has privacy controls for federal Information systems and companies – as a result, the revision 4 that publish Jan 2015; it is a draft revision 5, which is available.
Additionally NIST structure for updating Critical Infrastructure cyber security tools- version 1.1, that published in April 2018.
This Document intended to guide cyber care risk management in critical Infrastructure in US.
PCI DSS
Payment card Industry Data Security Standard, it is just like a security control, that needs to implement to secure payment account standard security. To explain It designed to protect the credit card, debit card, cash, and card transactions.
Coso
Stands for Committee of Sponsoring organizations of trend way commission.
5 popular Associations which go together with design this schema.
FEI – Financial Executives International.IIA - the Institute of Internal Auditors.AICPA -the American Institute of Certified public accountants.AAA – American accounting association.IMA, Institute of management accountants.
This shell designed on following core points, that is for reporting, auditing, controlling, and monitoring.
Uniquely structure has 17th core points, which categorize in five categories.
- Controlling and monitoring
- Communication and Information
- Control activities
- Risk assessment
- Control Environment
Equally this concepts combined and the policies built, However it adopted by employees and customize it according to business design. As a result it eventually guide operational and functional units.
TCCYBER
Known as the technical Committee on cyber security.
Equally Important this schema is updated and developed to provide, improvement within the telecommunication standards in Europe and adopted worldwide. Moreover It mainly focuses on privacy awareness and improves companies and Individuals.
NERC
North American Electric Reliability Corporation.
This structure is developed to make sure, that electric grids follow certain standards. In general, this framework adopts any of industry if needed.
specifically the issue with most common defense schemas is every time they involve in long PDFs. So, that it lead to more confusion, to define cyber care frameworks, which are very easier to understand. So, By the same token, He divided them into three categories. Risk frameworks, program frameworks, and control shells.
Similarly, Cyber defense professionals. Every time face problems when they are working. In the same fashion Thinking and understanding very much about cyber aegis is critical. For communication in easy terms, for outside of fields. However, cyber care frameworks were easier for everyone in the business standard.