
So with AWS Elastic Load balancing, we people can estimate this AWS platform is responsible for handling the large of data. And this large volume of data may contain any type of information. This includes both the normal information as well as confidential information. Moreover, an organization consists of huge number of people. And all these people will not belong to the same category in the organization. It means each organization will have many departments. And each department contains a group of members in the organization. So the organization admin needs to assign some permission to access the company data. And the organization does this according to the employee designation.
This is because we cannot provide confidential data access to the level users in the organization. So, in order to provide the data access to the employee across the organization, Amazon came up with a new idea known as IAM. This IAM is an acronym for Identity Access Management. With this concept, we can specify the policy rules for a specific group of people. So it means for every permission change in the group policy the same permission change will affect all the users in the group. It means an IAM is responsible for providing the necessary permissions to allows (or) deny access to the AWS resources.
What is an AWS IAM?
AWS IAM is generally defined s the Identity and Access Management. This provides the best service in providing the secured control access to all the AWS resources. Moreover, this IAM can authorize as well as unauthorized user access. So whenever you logged into the AWS Console, you will be entering as the root user.
How does IAM Work?
IAM works on some of the principles of the IAM infrastructure. Let us discuss these elements in detail.
Principle:
The AWS IAM is nothing but an entity. This is responsible for taking the action of the AWS resource. The Administrative IAM is the first principle, which allows the user for the particular services. Besides, here you can also deny the support to the federated users to allows access to your AWS Account.
Request:
Whenever if you are trying the principle to the AWS Management Console. the API (or) the CLI will automatically send the request to the AWS. This request may contain the following information
- Actions are considered as principles to perform
- Actions were performed based on the resources
- Principle information includes the environment, where the request has made previously
Authentication:
This is one of the most common principles used while signing into AWS while sending the request. Moreover, it also contains alternative services like Amazon S3. This Amazon S3 platform is responsible for allocating the request from the unknown users. So in order to authenticate from the console, you need to sign in with the login credentials like username and password. Besides, in order to authenticate, you need to provide the secret as well as the access key in addition to the required additional security information.
Authorization:
While authorizing the IAM values from the request, the AWS platform will check all the matching policies. And further, it evaluates whether to allows (or) deny the request. Moreover, all the policies stored in IAM as the JSON documents and offer specific permissions to other users. Among all the request AWS IAM checks all the policies that particularly match the context of all the policies. And if a single action is denied, AWS IAM denies the entire request and regret to evaluate the remaining ones. And this concept is known as the explicit deny.
Actions:
After processing the request to authorize (or) unauthorize, AWS automatically approves your action in the form of request. Here all the actions were defined by the services and things can be done by the resources. This includes creating, editing, deleting as well as viewing the application. So in order to allow the action principle, we need to include the required actions into policy without affecting the existing resource.
Resources:
On the basis of the resources in your account, AWS approves all the actions to your account. In general, a resource is known as an entity that exists particularly in the service. And this resource service can be defined as a set of activities that are performed on each and every resource. So in order to create one request, you need to perform the unrelated action that cannot be denied.
Click the link to know how to Empower your business with AWS IAM
So, now we will create the IAM role practically
step -1:
Login to your AWS account and search for IAM and you will be entered into the following screen
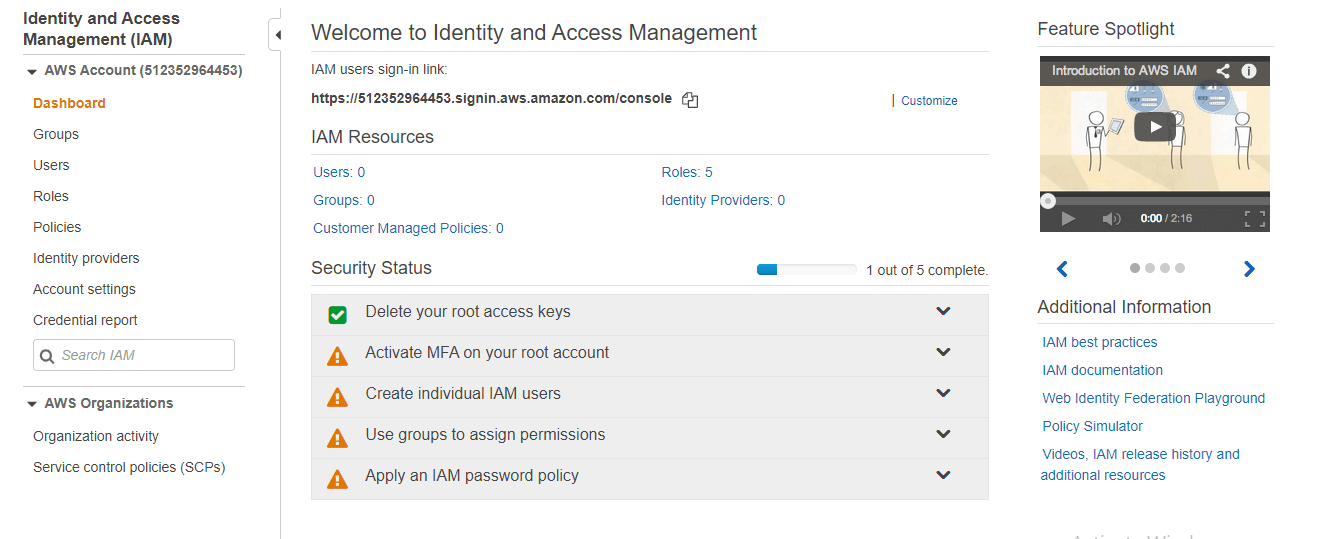
step -2:
Click on Groups
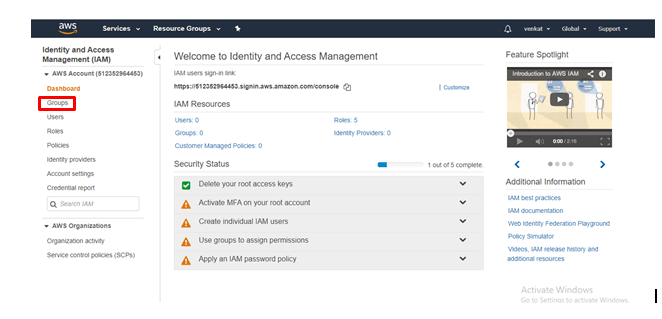
step -3:
Click on Create New Group
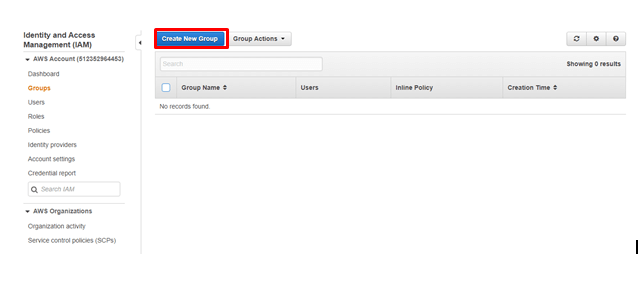
step - 4:
provide the group name and click on Next Step
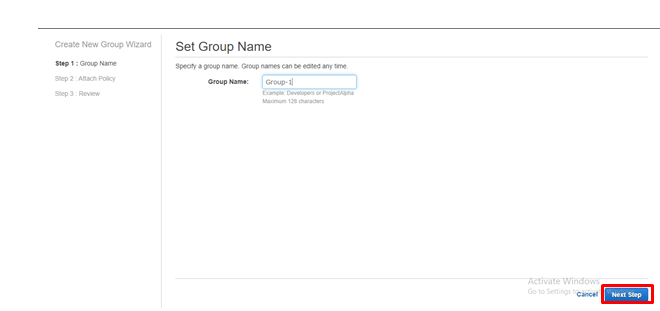
step- 5:
Select the policy type. Here, for instance, I would like to select the EC2 Full Access and click on Next Step.
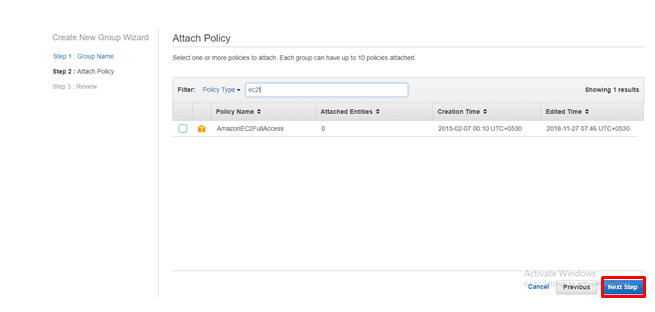
step - 6:
Click on Create Group.
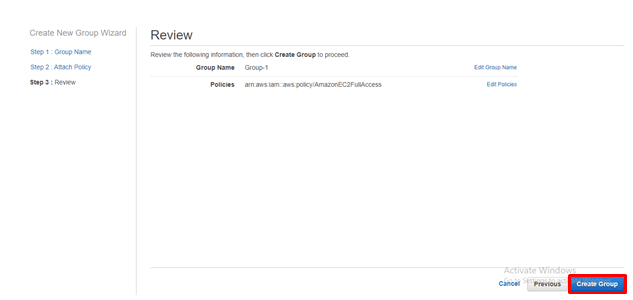
Since the group was created, we people need to add users to this group.
step - 7
Click on users
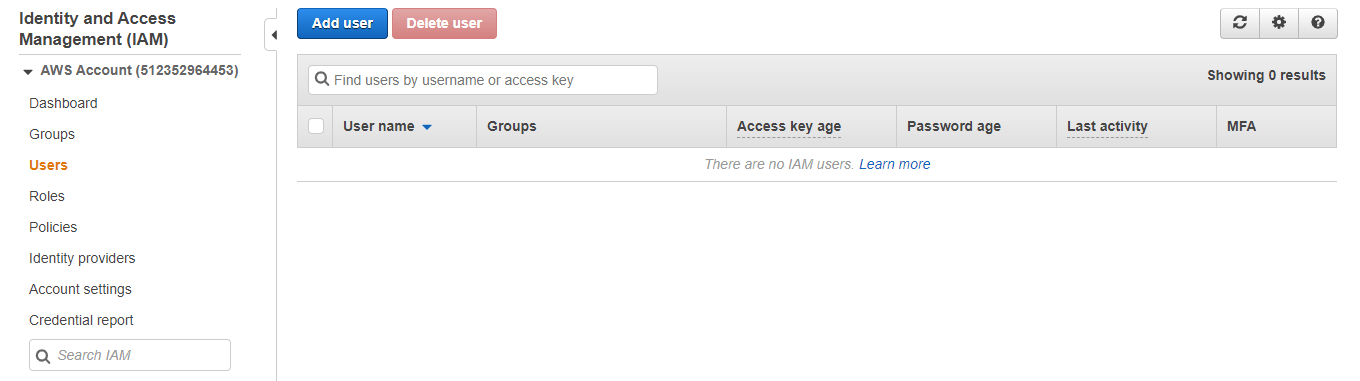
step - 8:
Click on Add user
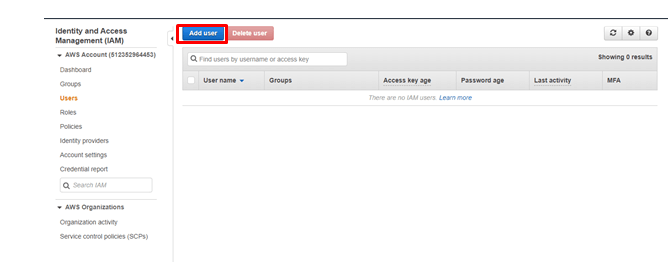
step - 9:
Provide the username and provide the access permissions. And also click on the console password and then click on permissions.
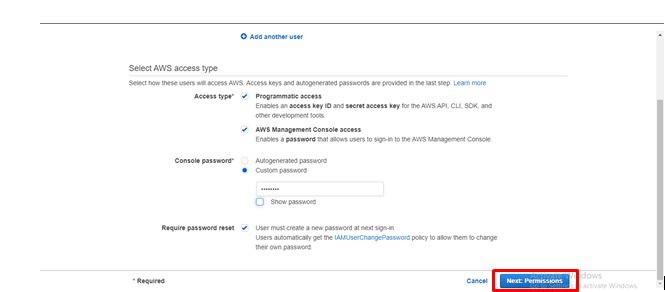
step -10:
Select the group and click on Tags.
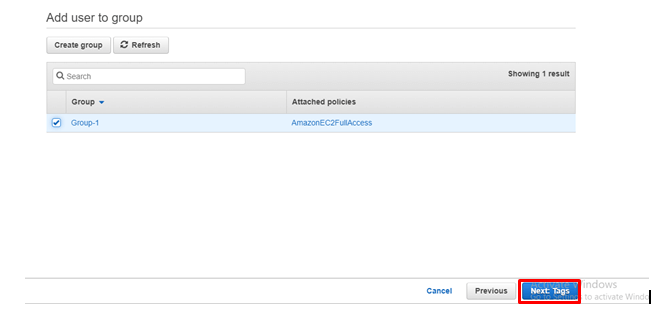
step - 11:
Provide the key-value pair and click on Review
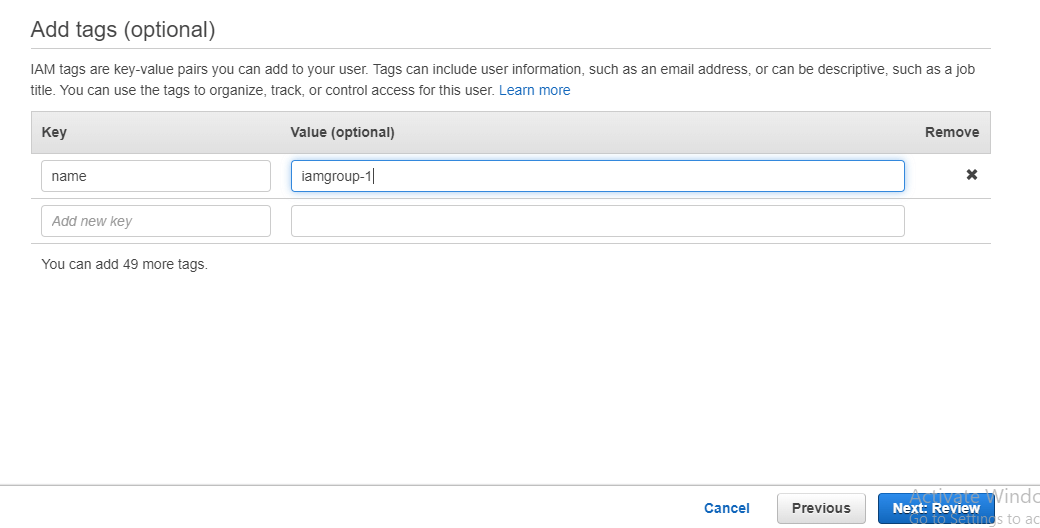
step - 12:
Check all the details that you have created till now and click on Create User.
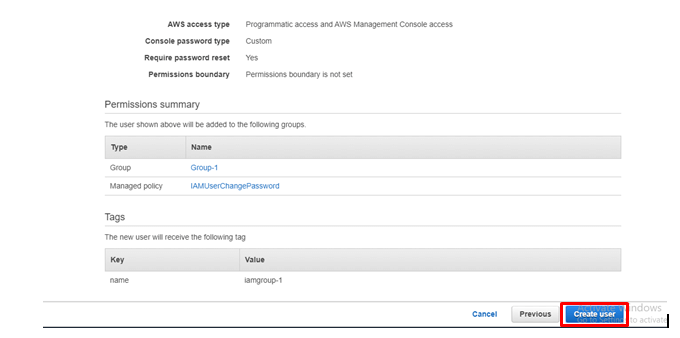
step - 13:
Click on Download.CSV and download the file
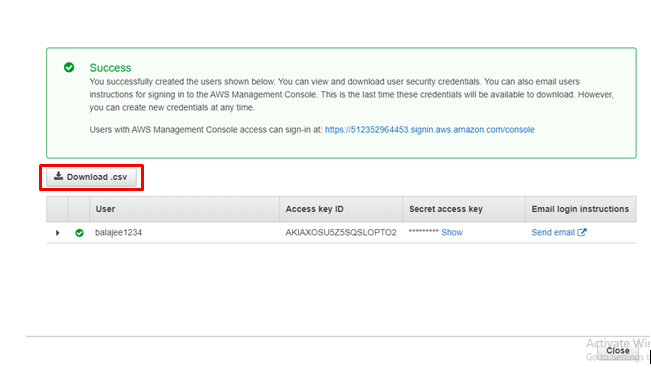
step - 14
Click Close
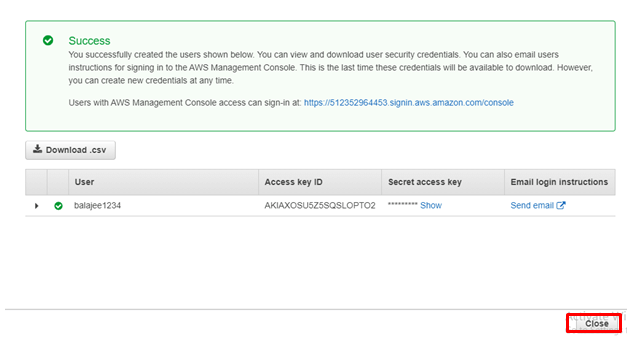
step -15:
Log in to the AWS console with the link that you have provided in the.CSV file.
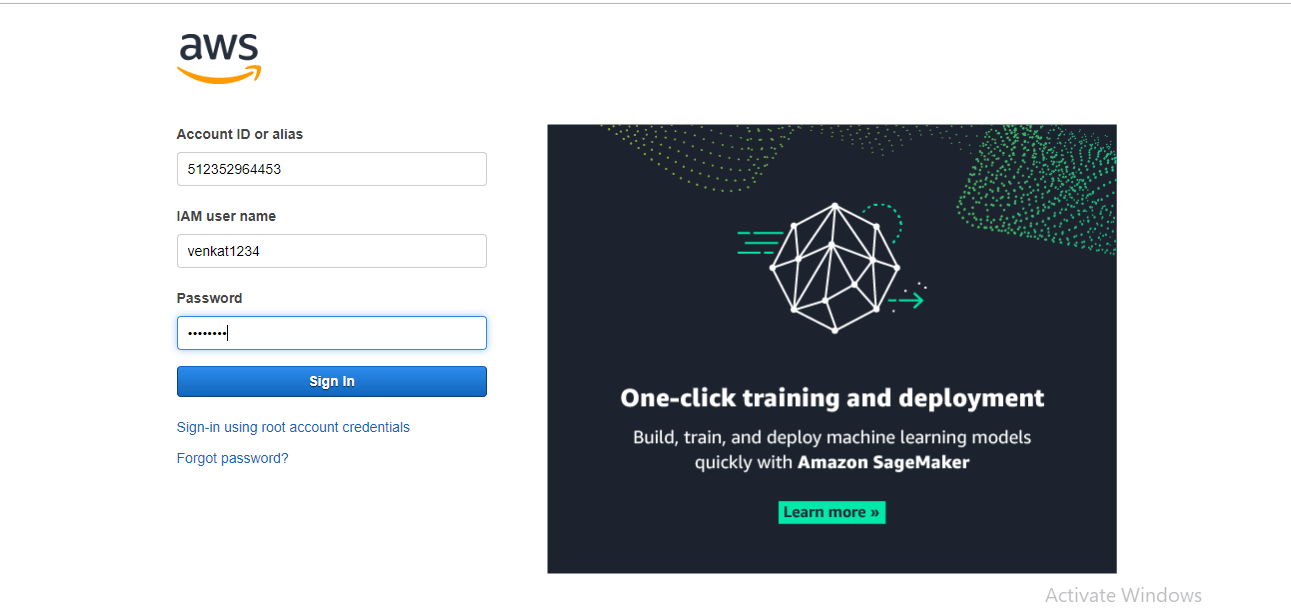
step - 16:
Then you will be entered into the following screen
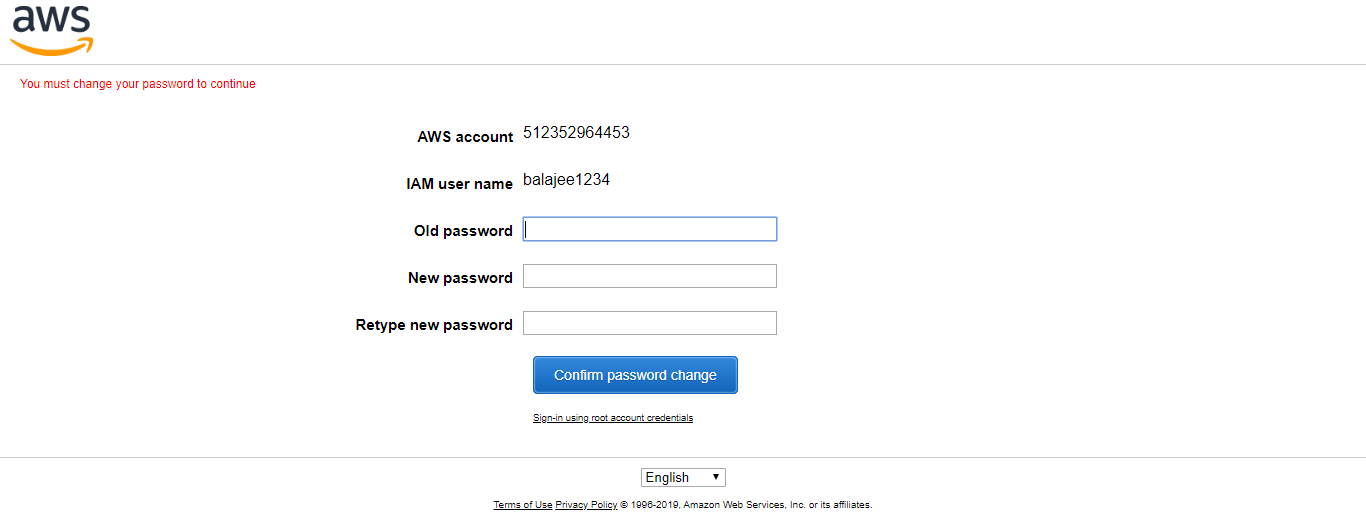
Create the new password and click on Confirm Password Change.
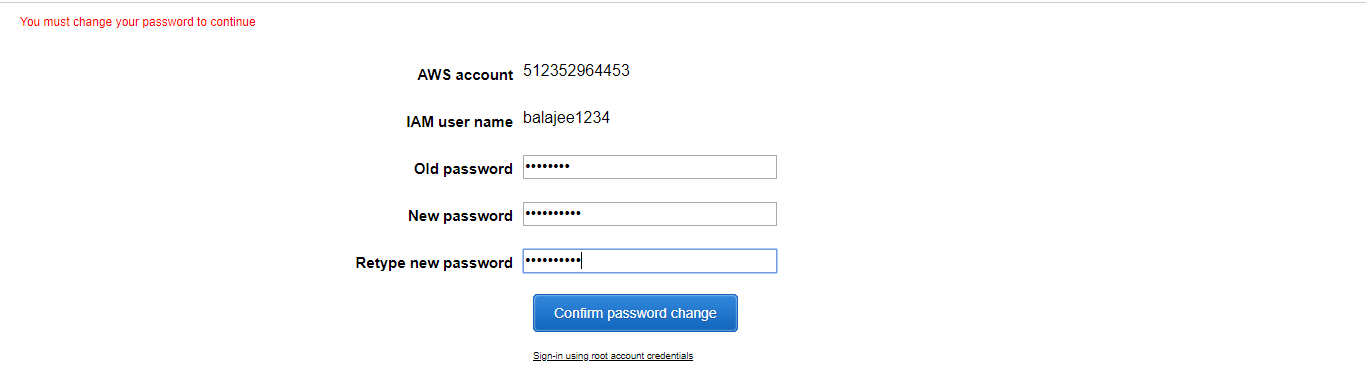
Step -17:
Then you will be entered into the following screen
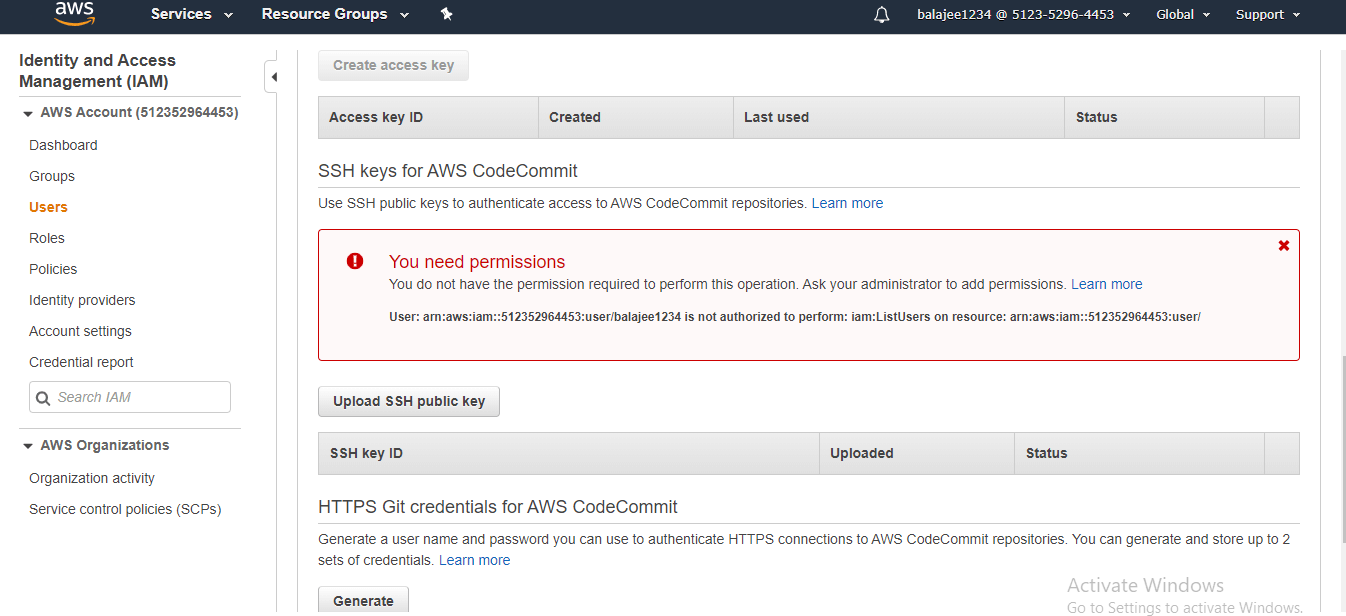
step - 18:
Click on Services and select EC2 and start creating an instance.
Click AWS instances to know about the instance creation
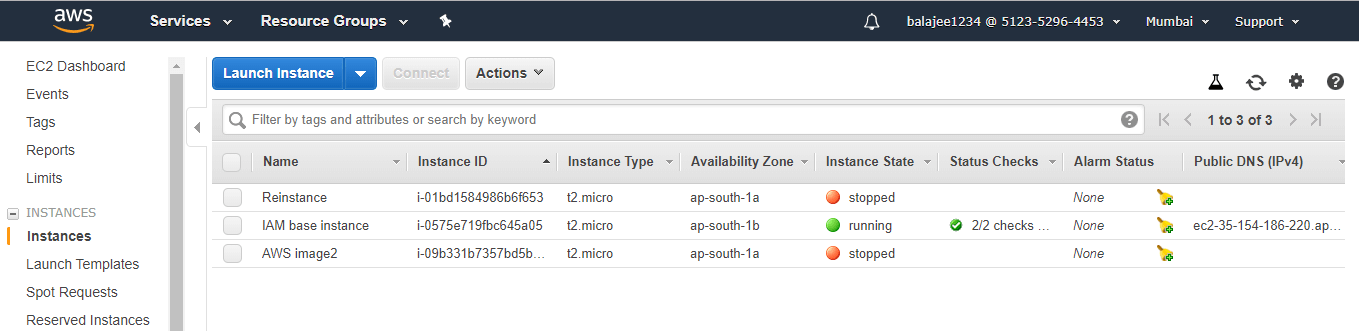
step - 19:
Once created, click on Instances, then you will be entering into the following screen
And if you try to access the other services (For instance S3) then you will get the error as follows.
If
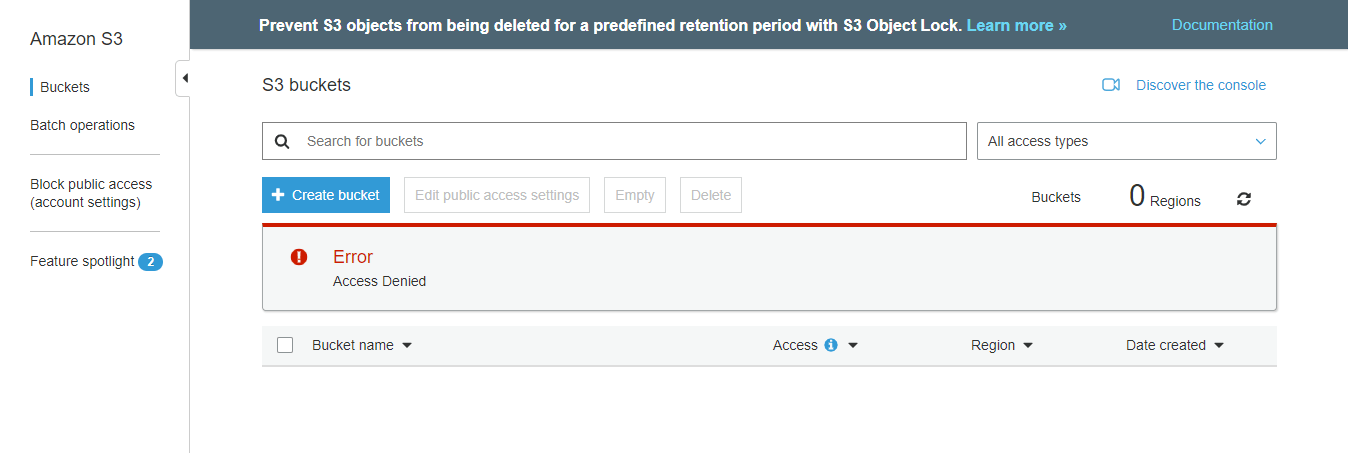
If you struck up anywhere feel free to contact AWS Online Training
What are AWS IAM Roles?
AWS IAM Role is the same as the user with the AWS identity with certain policy permissions. These policies determine the specific identity that can (or) cannot be with AWS. So one can use similar roles to delegate certain access to the users, applications (or) other services to have access to these resources.
AWS IAM provides the following rules
- Increasing the security as well as protection of certain AWS resources and also the configuration of multi-factor authentication
- Enabling of MFA on root accounts as well as the privileged users
- Multi-factor authentication can be configured with ease.
1. Security Token-Based:
IAM Users (or) the AWS Root users were mostly assigned to the hardware (or) the virtual MFA devices. Moreover, based on the synchronization of One-time password (OTP) algorithms, it can easily generate the six-digit numeric code which is required at the time of process authentication
2. SMS text message-based (preview -mode):
- With a user phone number, IAM users can easily config with SMS compact able mobile devices. And these devices will receive the 6-digit code from the AWS platform.
- SMS based MFA is available only for IAM users. But this feature does not work on the AWS root account
- Since the root users as well as the IAM users with the separate entities, MFA needs to be enabled in the respective format. Moreover, MFA enabling on root does not enable it for all the other users,
- The MFA device will get activated only with one IAM user (or) the AWS account respectively
- Moreover, if the MFA device suddenly stops working (or) lost, there is no authentication to log into the AWS Console. So in this case, the person needs to AWS support team for MFA deactivation
- MFA protection is easily enabled for the respective service API calls using Condition Bool. This gives support to the temporary security credentials
Features of IAM:
AWS IAM provides the following services
Shared access to your AWS Account:
In your AWS Account, this platform allows you to share the resources with other AWS Accounts without sharing the password.
Granular permissions:
Using the granular permissions, this platform grants the permissions to different resources. For instance, this platform allows you to provide the whole access to Amazon EC2, S3 as well as to the other AWS services. Moreover in the process of billing the information, this platform allows you to provide the read-only access with the administrator EC2 instances.
Secured access to the AWS Sources:
This AWS IAM feature is responsible to maintain the security for all the login credentials on the EC2 Instances. Besides, you can also offer various permissions, in order to access your application w.r.t the AWS Services.
Multi-Factor Authentication:
In order to provide more security, the AWS platform uses Multi-Factor Authentication(MFA). With MFA you can easily add the two-factor authentication not only to your account but also to the individual users. Here any of our team can provide the access key (or) password to work with our account. And we can provide this with the code that is specifically configured by the device.
Identity Federation:
It means this platform allows the user to login to the AWS Console with several social networking sites. This includes Facebook, LinkedIn, Active directory and so on. It means, the users can log in to these accounts with the same username and password as like the Facebook, Active directory and LinkedIn
Identity information for Assurance:
If you are using the cloud trail option to your AWS account, you people will definitely get the log records. And these logs contain all the information that is made according to all the resources in your account. And this information was generally named as IAM identities.
PCI DSS Compliance:
The AWS IAM will completely support all the storage, transmission by both the provider as well as the merchant. This supports in order to validate the complaint with the Payment card Industry (PCI). Data Security Standard (DSS). For instance, if you were taking the credit card information, you need to pay for compliance with the framework.
Eventually Consistent:
IAM service is eventually consistent, it means it achieves high availability by replicating the data across multiple servers within the amazon data center across the globe.
Networking Controls:
IAM ensures that users can access the AWS resources, within the organization corporate network.