
There is always a lot to learn when it comes to getting any form of software, regardless of how long you have been using Workday. Is there a portion of Workday functionality that needs your special attention? permissions for security.
The information in your Workday platform is crucial to your organization on two levels: for the people who operate it and for the operation of the business itself. Because of this, every wise firm out there makes safeguarding your data and making sure it complies with legislation a top concern. Managing data privacy and sensitive data protection is, of course, sometimes easier said than done, particularly when new security concerns and continuously evolving rules are taken into consideration.
It can be difficult to maintain track of sensitive data that needs a special encryption key while balancing the roles of your data processor and data controller, especially if you're also trying to deploy or integrate Workday modules into your system. Having to deal with so many facets of data organization and security at once leave you unsure of how to proceed. You'll require a dependable Workday security administrator in that situation.
Want to learn Workday from the basics? enroll for Workday Online Training
Here's a library comparison to help clarify how Workday's security functions.
How Does Security in Workday Work?
For this illustration, imagine that each employee has a login that entitles them to a book loan from any networked library branch, provided that Workday security permits them access to that book. The map below illustrates how the library network is set up to have various types of data (or "books") in each location.
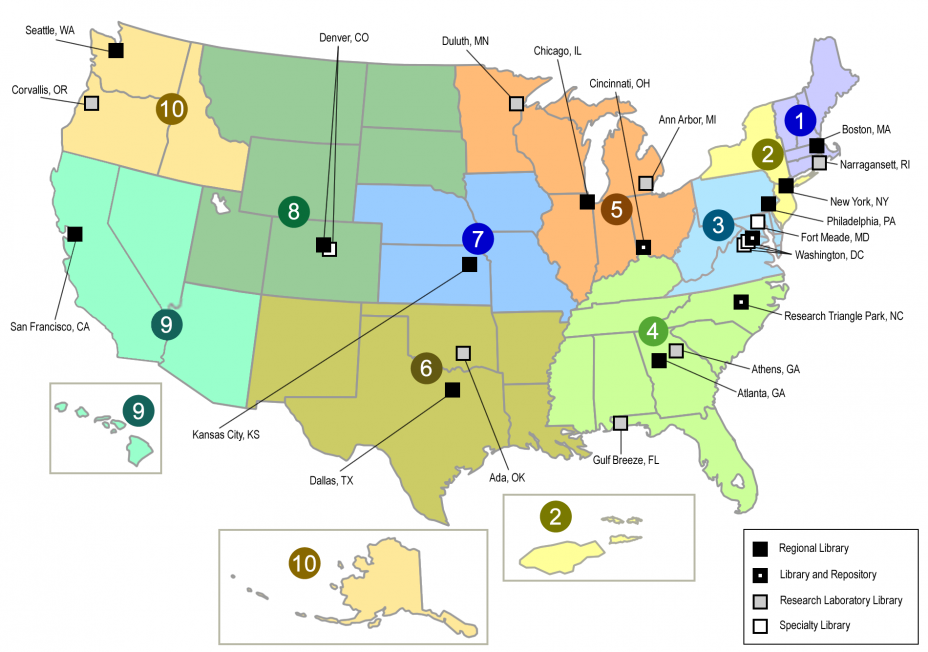
Here is a possible storage and separation method for some of your data. (Remember that this is a condensed example. There are numerous data domains in Workday.)
Region 1 – Payroll Data
Region 3 – Personal Contact Information and Demographics
Region 4 – Compensation
Region 9 – Job history records
Region 10 – Benefits data and history
For this illustration, imagine that each employee has a login that entitles them to a book loan from any networked library branch, provided that Workday security permits them access to that book. The map below illustrates how the library network is set up to have various types of data (or "books") in each location.
Here is a possible storage and separation method for some of your data. (Remember that this is a condensed example. There are numerous data domains in Workday.)
Understanding Workday Security Roles
Customer data, compliance standards, and processing operations are constantly changing, so your team needs to be able to stay up with them whether you're new to Workday or have been using it for some time.
Making sure all employees have access to the information and tools they require to do their duties is an important step for any organization. They require access to certain system data, but it's also critical to prevent that data from falling into the wrong hands. Workday security roles are useful in this situation.
What Exactly Are They?
Workday's security roles assist your company and its administrators in maintaining constant surveillance of the data entering and leaving the system. They manage an employee's security permissions generally, as well as their capacity to initiate processing activities, approve data transactions, and update data. Security roles in Workday define the precise access each employee has to data, reports, and other insights and functions within your organization, even though they are identical to your organization's basic data protection regulation processes.
How Are They Different?
In Workday, security roles are assigned and differentiated based on an employee's job rather than by them individually. By doing this, you make it slightly easier for yourself to deal with the security difficulties that result from employees leaving your company or changing positions. Additionally, it removes any extra processes that are needed for data transfers, security updates, or employee changes, while yet protecting your data. That is what role-based security in Workday aims to achieve.
Making Changes to Workday Security
Let's consider the security ramifications of changing data in your Workday system in greater detail. At that point, you must pay close attention to the point where Workday Security and Business Processes meet.
Your business processes define who can initiate a transaction, view a change onboard (before it's fully approved and committed to the database), undo the changes and restore values to their previous states, and perform approvals in addition to defining what occurs in your Workday organization (such as validation, approvals, and notifications).
However, rather than using a Business Process, some types of data must be modified through a Task. Administrative tasks—like introducing a new cost center—can be performed by anyone who belongs to a security group that is authorized to do so.
Creating Security Groups in Workday
Making security layers that cooperate is another approach to getting the most out of your Workday security features. Say, for instance, that you want a Sales Ops employee who doesn't have any direct reports to be able to view remuneration, including commissions, but only for salespeople.
One approach to do so is to make a new custom security group, including the Sales Ops team in it, and then apply to that group a set of security rules that permits access to compensation information for staff members who have a compensation plan assigned to them that permits commission payments. In this sense, security is defined by compensation plan assignment rather than by domain or management hierarchy.
Want to know more information on security groups? Enroll for Workday Online Course
Workday Security Best Practices to Keep in Mind
Here are a few best practices to remember to get the most out of Workday security now that you have a better understanding of its fundamentals. Some of our suggested Workday security best practices are listed below:
Regularly check user-based security groups to make sure no one has access to areas they shouldn't.
Keep an eye on your baseline security posture and make sure to regularly log any changes you detect. This is especially important with the growing relevance of GDPR compliance and regulation.
In addition to your regular monthly testing, there are other crucial periods to assess your security environment. Whenever a worker is added to multiple groups (and consequently has access to multiple different security areas) or security groups are changed, during implementation and testing, after adding new functionality, or both, you should always test to ensure that no one has been given improper security access.
A Few Common Mistakes to Avoid
Complicated Security Groups
The finest piece of advice anyone can give is to make Workday Security straightforward. Many organizations have fallen into the habit of making improvements to address every single complaint, only to find that after adding numerous new features, the system has more issues than before.
Keep your security remedies straightforward. When you do implement privacy and security constraints, try to steer clear of Security intersections with an excessive number of exclusions. Particularly as you attempt to manage your change management strategy as your business grows and people come and go, making it simpler to determine who has access to what is crucial.
||{"title":"Master in Workday", "subTitle":" Workday Online Training by ITGURU's", "btnTitle":"View Details","url":"https://onlineitguru.com/workday-training.html","boxType":"reg"}||
The general data protection regulatory plan for your business must have a way to handle change and troubleshoot data problems. Simplifying this process will assist save your employees, administrators, and the entire organization time, resources, and quite a few headaches since data protection is crucial to the success of your business.
Improper Setup for Integrations
Keeping things straightforward is the key to success when it comes to integrations within your Workday system. When a process is made more difficult by adding too much information or restricting access to certain account types, you create a new set of issues that could have been easily avoided.
Too Much Information
Implementers frequently make the error of trying to make an integration work with everything. To put it another way, if you're creating an integration that depends on security to function, make sure it has only the access necessary to carry out its task. If not, it's essentially like tossing shattered glass into the road in front of your vehicle and praying you don't hit it later.
Too much information at one step of the process will not only confuse you later but may also slow down your Workday implementation or integration process. Time is money, as we all know, therefore being able to manage the timeline of your business operations and regularly monitor integrations is crucial to your success, particularly given the rapidly evolving data and security market.
||{"title":"Master in Workday", "subTitle":" Workday Online Training by ITGURU's", "btnTitle":"View Details","url":"https://onlineitguru.com/workday-training.html","boxType":"reg"}||
Issues with Personal User Accounts
Allowing integrations to operate under personal user identities is another way one observed clients mess up their integrations. In the past, we've seen instances where integration was configured to function as a separate user account. That worked—until the individual departed the organization. The business disabled their account as was customary, which also led to the failure of the integration.
Understanding the appropriate methods to handle your integrations early is crucial because lessons like these can be time-consuming and stressful for businesses to master.
Lack of Documentation
The importance of documentation for security cannot be overstated. You must create a plan for how requests will be received, what will be examined and given priority, and how work will be completed. You must also document this plan. You could have a clear idea of what you're attempting to do right now, but what about a month from now? An undocumented strategy is like trying to assemble a puzzle after tossing away the box. What will happen in ten months?
A well-written strategy will spare you headaches in the future and guarantee that everyone working on the project has something to refer to as the project moves forward. Each employee will be held accountable in this way, ensuring that nothing slips through the cracks and needs to be fixed by a subsequent employee.
Conclusion:
By reaching the end of this blog post, I hope you people have written enough ideas on Workday security practices. You, people, can get a practical explanation of these security principles from real-time experts through Workday Training. Contact the OnlineITGuru support team today and register for a free demo sessional